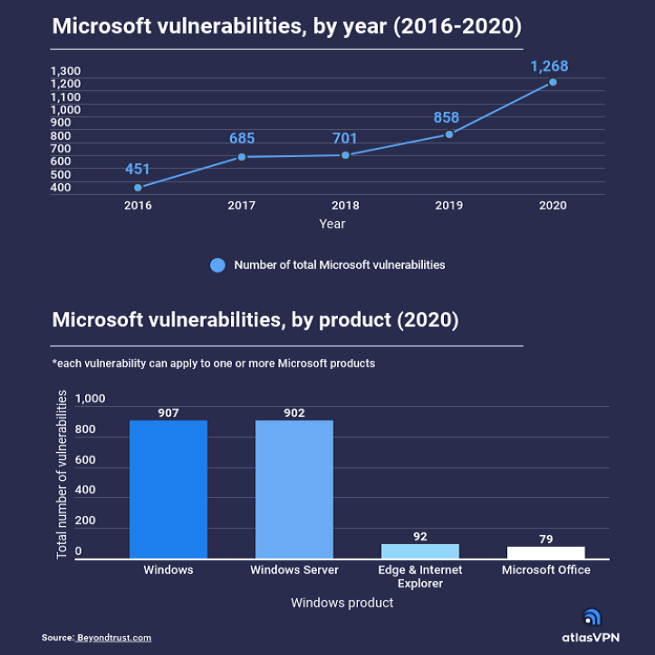
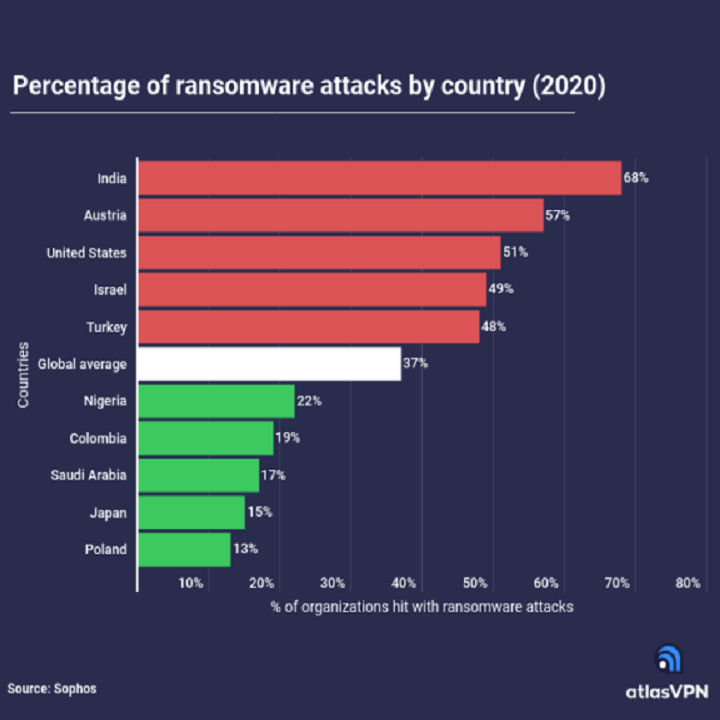
In the current age of digital technology, car owners are being forced to consider their vehicle’s susceptibility to ransomware attacks. These malicious cyber-attacks can expose your personal data to online hackers. However, there are certain measures that car owners can take to help prevent security breaches. Proactive car owners are utilizing services like Concentric to […]