Adam Anderson, the author of “Fire Yourself, the Entrepreneurial Endgame” and co-host of the “Two Stones, One Bird” PODcast, is a cyber security and space entrepreneur who has been the advisor, founder and/or primary investor in over 30 startups.


Adam Anderson, the author of “Fire Yourself, the Entrepreneurial Endgame” and co-host of the “Two Stones, One Bird” PODcast, is a cyber security and space entrepreneur who has been the advisor, founder and/or primary investor in over 30 startups.

By: Casey Allen with Concentric Where there is commerce, thar be pirates! The techniques, tactics, and procedures of modern-day pirates have expanded significantly since the Lukkan buccaneers first raided Cyprus back in the 14th century. The practice of maritime piracy is still alive and well, but as technology has advanced from bronze to blockchain the […]
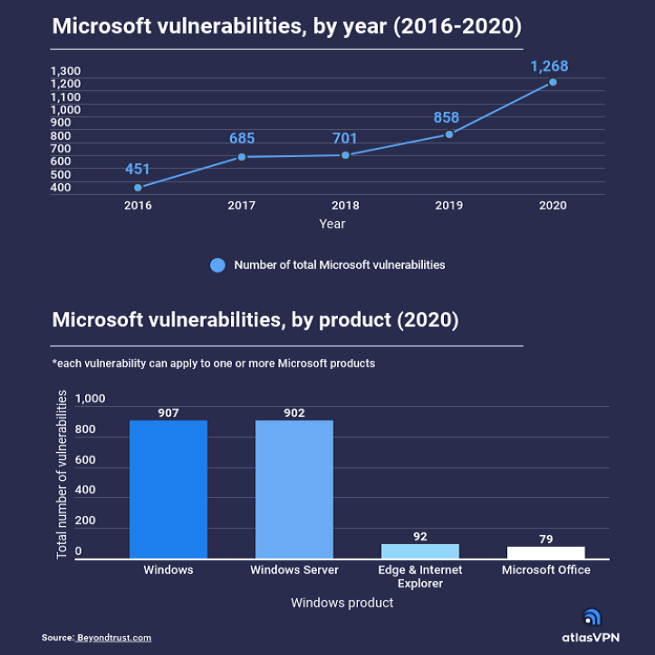
Microsoft products are used by billions of people worldwide. Historically, however, they are known to have many vulnerabilities that pose security risks to users of the software. According to data presented by the Atlas VPN team, the total number of vulnerabilities in Microsoft products reached 1,268 in 2020—an increase of 181% in five years. Windows […]
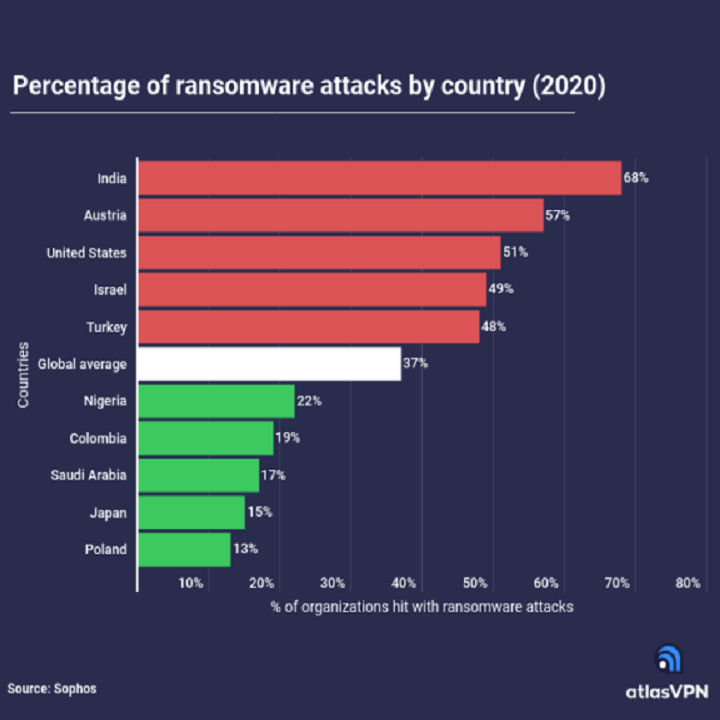
Ransomware attacks are one of the leading cyber threats that organizations have to face. According to the data presented by the Atlas VPN team, organizations in India, Austria, and the United States are among the most hit with ransomware attacks. To compare, more than 50% of companies in the mentioned countries experienced such attacks in […]

Many Internet users don’t take online privacy seriously because they believe that they have nothing to hide. Even if you don’t want to secure your data from the curious eyes of big brother, you should be aware of other privacy threats on the Internet. Other states: Even if you trust your own government, do you […]

We live in times when it’s become easier than ever for hackers to breach an organization through social engineering. Breaches are primarily caused by phishing attacks, representing a huge security problem for businesses. But why is this type of cybercriminal so widely represented in the statistics? What is it that makes it so easy and […]