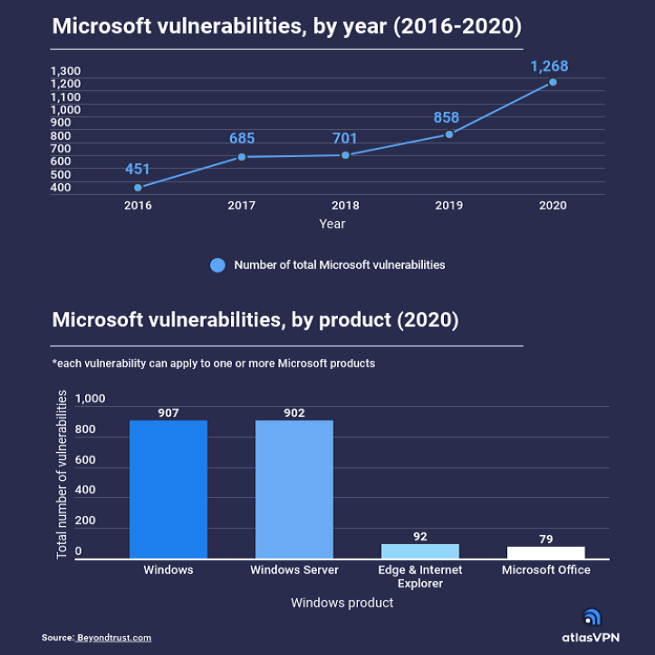
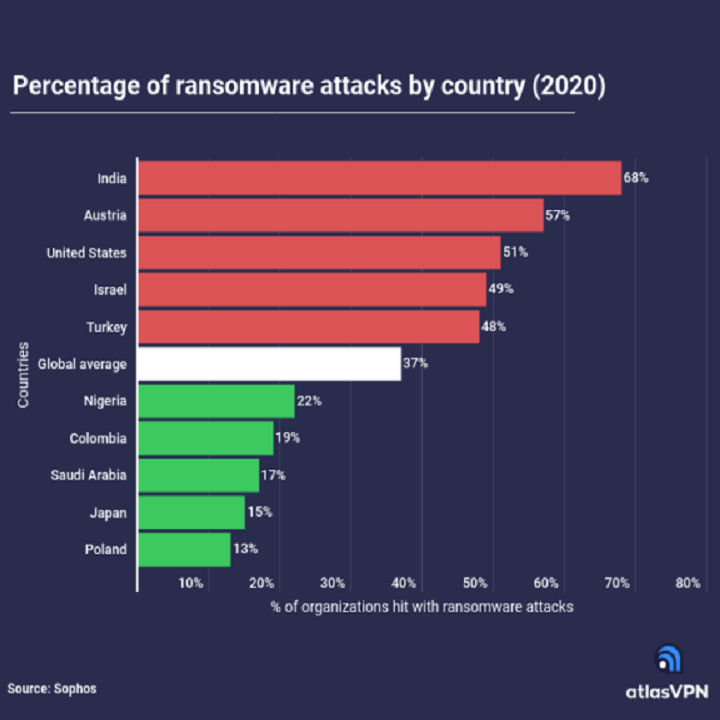
Online gaming should be a fun and rewarding experience that, critically, does not have any lasting impact. Staying safe online is vital, especially when gaming, as it is all too easy for a fun and innocent activity to become malicious when the right steps have not been taken. That does not mean to say that […]