Femme is an artistic yet rivoting tale enunciating gay social constructs within Great Britain.


Femme is an artistic yet rivoting tale enunciating gay social constructs within Great Britain.

A smart home can be such a massive help for a busy family. They automate several processes in daily life so you don’t have to take the extra time to do them yourself. A smart home assistant can keep notes for your next grocery order, and a smart outlet can help you save energy and turn your lights on and off with a single command in your phone.

As a multi-media, multi-blockchain NFT Creation Engine and marketplace wrapped in a social ecosystem that streams NFT music, live streams and post, SIKI app is one of the fastest-growing companies in the blockchain/crypto space. SIKI is in a private “invite only” stage currently which users can apply for. Despite so, the app is already packed […]

Jankel and Williams Advanced Engineering collaborate to bring EV technologies and capabilities to the US Defence market Jankel and Williams Advanced Engineering (WAE) are collaborating to bring EV technologies and capabilities to the US defence market The partnership will combine complementary technologies and capabilities to help progress military hybrid and electrification projects The partnership will […]
By: Andrew Shibuya As the world has remained in their homes this past year and a half, traveling abroad seems to be the light at the end of a very long tunnel for many. While globetrotters stayed home bound and planned their trips for the second restrictions lifted, the travel industry underwent a rapid and […]

When a developer leaves a mistake in application code, it can create a security vulnerability that criminals may exploit. According to the data presented by the Atlas VPN team, 63% of Android applications had known security vulnerabilities in Q1 2021, with an average of 39 vulnerabilities per app. Gaming apps had the most vulnerabilities out […]

No one likes being watched, offline or on. And it is especially unnerving when a brand oversteps that boundary and pops up everywhere you go online. Invisibly is on a mission to ensure companies have your direct consent for using your data and compensate you for the use of it. Invisibly believes in Seven Core […]

In the current age of digital technology, car owners are being forced to consider their vehicle’s susceptibility to ransomware attacks. These malicious cyber-attacks can expose your personal data to online hackers. However, there are certain measures that car owners can take to help prevent security breaches. Proactive car owners are utilizing services like Concentric to […]

According to a recent study by the Atlas VPN team, the United States, United Kingdom, and Saudi Arabia lead in commitment to cybersecurity. As technologies continue to evolve, governments around the world must face the reality of cyber threats and adapt their security practices. A study reports on countries’ scores on the Global Cybersecurity Index […]
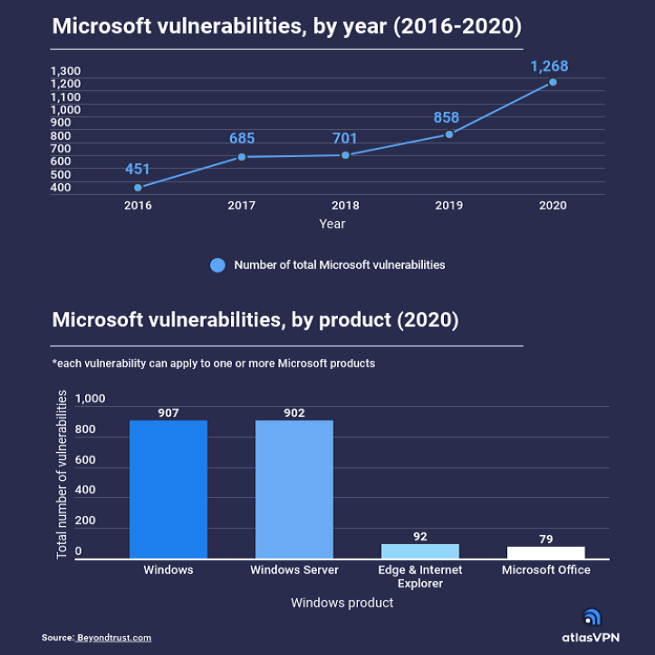
Microsoft products are used by billions of people worldwide. Historically, however, they are known to have many vulnerabilities that pose security risks to users of the software. According to data presented by the Atlas VPN team, the total number of vulnerabilities in Microsoft products reached 1,268 in 2020—an increase of 181% in five years. Windows […]